Android enforces screenshot restrictions on apps displaying sensitive data, such as banking platforms or DRM-protected streaming services. These limitations stem from FLAG_SECURE, a system-level policy that blocks screen capture to prevent unauthorized data extraction. While this enhances security, users often require legitimate access to visual information. Below are three actionable methods to circumvent these restrictions without compromising device integrity.
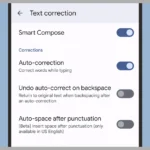
Disable FLAG_SECURE via Developer Options
Developer Options provides access to Android’s debugging tools, including settings that override app-specific restrictions. Enabling USB debugging grants temporary control over security flags for testing purposes.
- Activate Developer Options by tapping Build Number seven times in Settings > About Phone.
- Navigate to Developer Options > Debugging > Enable USB Debugging.
- Connect the device to a computer via USB and use ADB commands:
adb shell settings put global enable_screenshot 1.
This method requires Android 11 or later and revokes itself after a reboot. Use it only for short-term capture needs, as prolonged USB debugging increases vulnerability to external attacks.
Leverage Third-Party Screen Capture Utilities
Apps like AZ Screen Recorder or ScreenCam bypass FLAG_SECURE by accessing framebuffer data directly. These tools utilize Android’s MediaProjection API, which captures screen content independently of app-level restrictions.
- Install a trusted screen recorder from the Google Play Store.
- Grant necessary permissions via Settings > Apps > Special Access > Display Over Other Apps.
- Initiate recording before launching the restricted app to capture real-time activity.
Some banking apps detect MediaProjection usage and may force-close. Test compatibility by recording non-sensitive apps first.
Use Secondary Devices or Emulators
Physical workarounds eliminate software conflicts entirely. Mirroring the screen to a secondary device via Chromecast or HDMI allows capturing content externally. Alternatively, Android emulators like BlueStacks or Genymobile ignore FLAG_SECURE in virtualized environments.
- Connect Android to a PC via scrcpy for wireless mirroring.
- Use screen-sharing hardware to project content onto an external monitor.
- Install restricted apps on emulators and capture freely via host OS tools.
This approach avoids modifying the primary device’s configuration but introduces latency and requires additional hardware.
Analyzing FLAG_SECURE Implementation
FLAG_SECURE activates a hardware-backed security layer that encrypts framebuffer data. Apps triggering this flag include banking clients (e.g., Chase Mobile) and streaming services (e.g., Netflix). Android 13 expanded this to cover select notifications and autofill dialogues. Kernel-level enforcement ensures even rooted devices cannot bypass it without system modifications.
App-Specific Limitations and Risks
Banking apps using Android Keystore or SafetyNet Attestation may detect third-party capture tools and suspend functionality. Screen recorders requiring accessibility services often trigger false positives in fraud detection algorithms. For enterprise-managed devices, circumventing security policies violates MDM agreements and may result in account suspension.